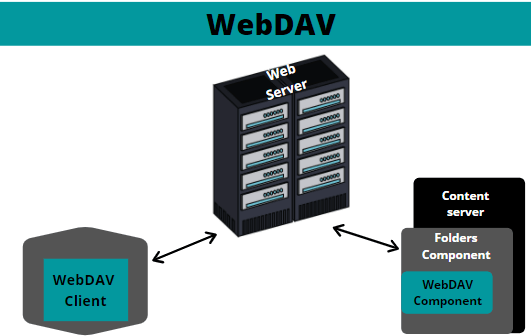
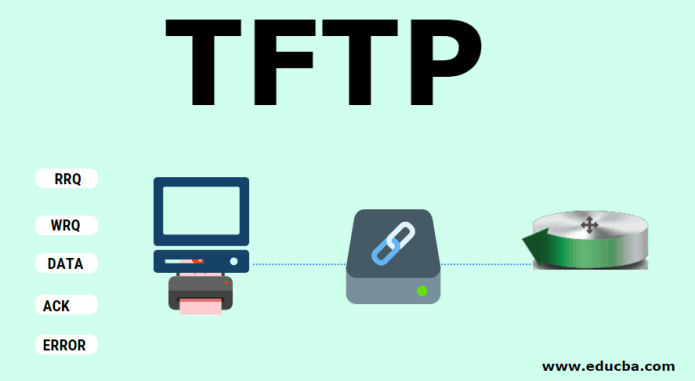
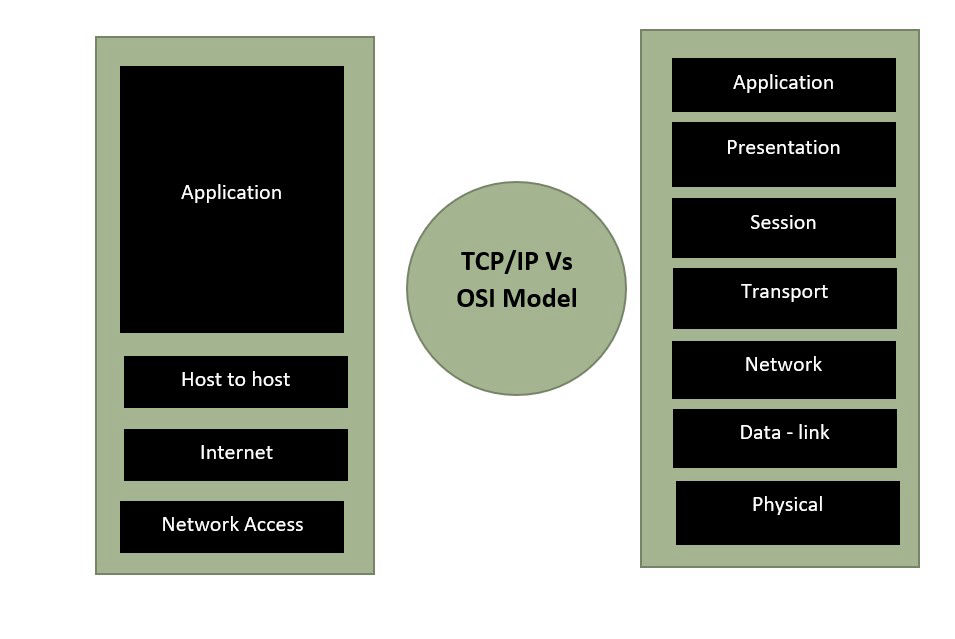
FTP
Description
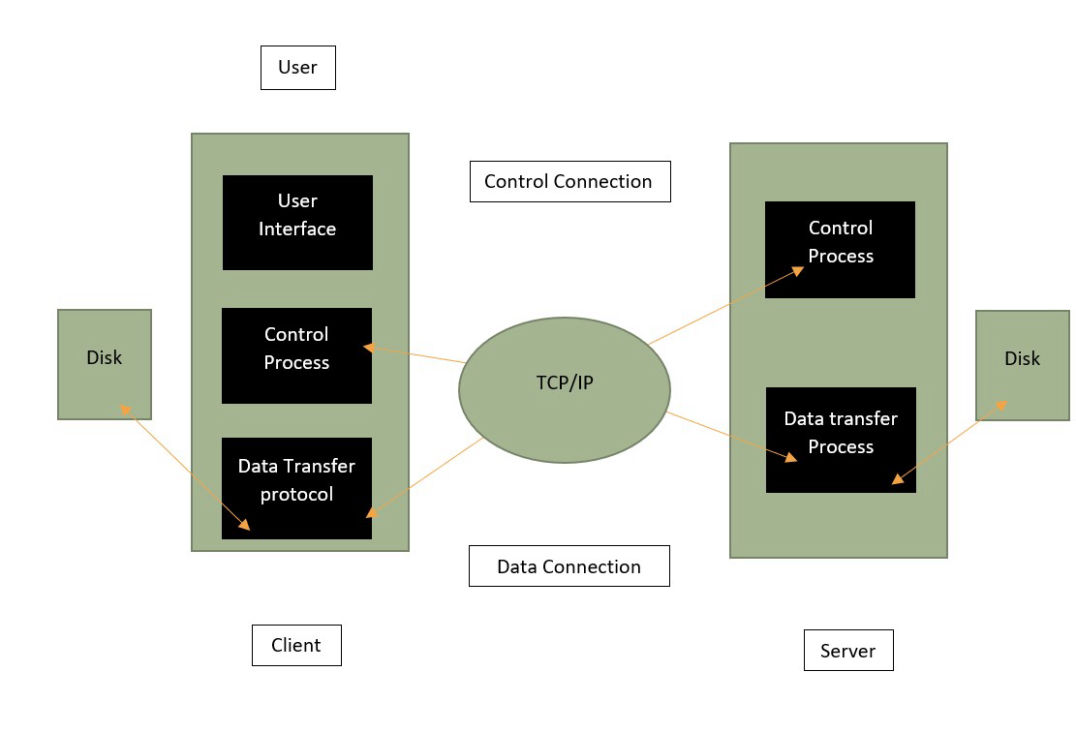
• FTP is used to transfer files from one system to another
over a TCP/IP network.
• FTP is an acronym for file
transfer protocol, which is used to exchange files over the
internet. It functions similarly to the HTTP protocol.
•
FTP is a method of sending and retrieving files over the
internet without the use of an email address or a password. It
transfers large amounts of data at once.
• In FTP, both the
sender and the receiver have the FTP host's username and
password. It only authenticates the authorised user.
• When
a user sends data to a recipient, the data is encrypted to
ensure data security.
• In FTP, there are two modes of
communication. The first is Active mode, while the second is
Passive mode. Both modes are used to safely transfer
files.